“Auto-Color,” a new Linux malware, grants hackers full remote access, targeting universities and governments in North America and Asia. It employs advanced evasion tactics, making detection and removal exceptionally difficult.
-
Nikita Alexander
- February 27, 2025
- 3 minutes

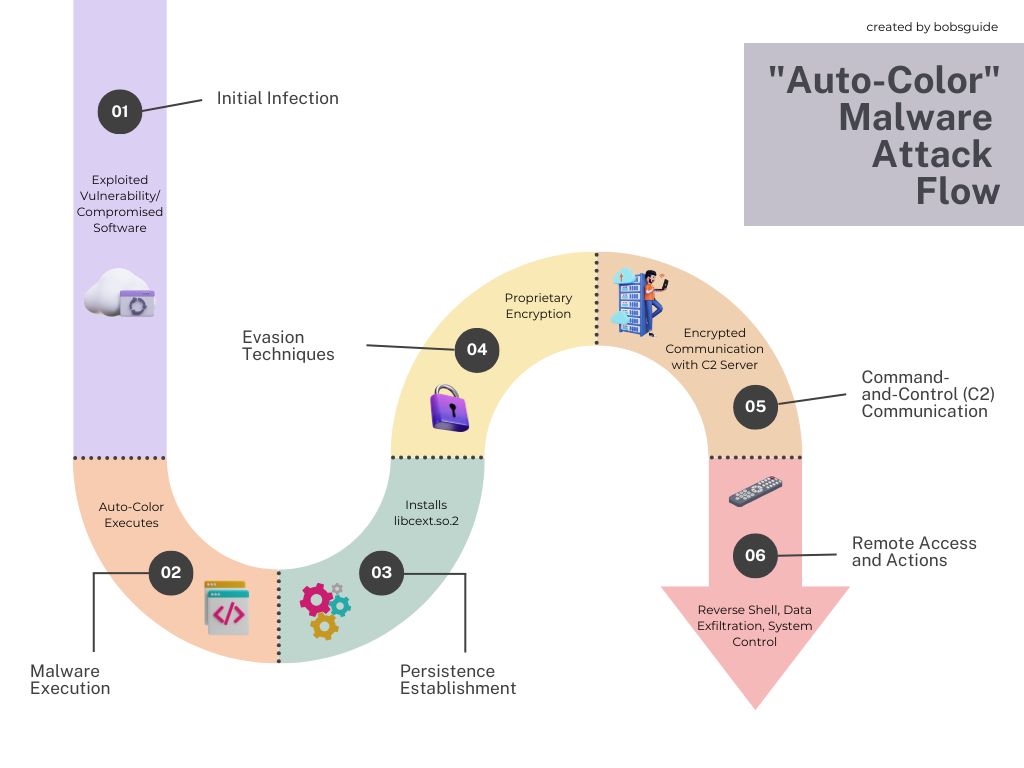
A newly discovered, sophisticated Linux malware, “Auto-Color,” has been actively targeting universities and government organizations in North America and Asia. According to research from Palo Alto Networks Unit 42, this malware grants attackers full remote access to compromised systems, employing advanced evasion techniques that pose a significant threat to critical infrastructure and sensitive data.
Findings and Technical Details
Targeting Specific Sectors:
- “Auto-Color” has demonstrated a clear focus on universities and government entities, indicating potential espionage or data theft motives.
- The geographical targeting of North America and Asia highlights the global reach of this threat.
Evasion and Stealth:
- The malware uses innocuous file names like “door” or “egg” to mask its presence.
- It leverages proprietary encryption algorithms to obfuscate command-and-control (C2) communications and configuration information, making detection challenging.It also hides C2 communications by modifying “/proc/net/tcp,” a file that contains information on all active network connections.
Persistence and Functionality:
- Upon execution, “Auto-Color” installs a malicious library implant (“libcext.so.2”), copies itself to “/var/log/cross/auto-color,” and modifies “/etc/ld.preload” for persistence.Even without root privileges, the malware attempts to establish as much functionality as possible.
- It prevents uninstallation by protecting the “/etc/ld.preload” against further modification or removal.
- It establishes a reverse shell, enabling attackers to execute commands, gather system information, manipulate files, use the compromised system as a proxy, and even self-destruct via a kill switch.
- “The threat actors separately compile and encrypt each command server IP using a proprietary algorithm,” security researcher Alex Armstrong noted, making it difficult for traditional antivirus software to detect.
Remote Access Capabilities:
- “Auto-Color” provides comprehensive remote access, allowing attackers to control compromised machines effectively.
- “Once installed, Auto-color allows threat actors full remote access to compromised machines, making it very difficult to remove without specialized software.” Stated Alex Armstrong.
Real-World Implications
Espionage and Data Theft:
- Targeting universities and government organizations suggests potential espionage activities, with the aim of stealing sensitive research data, intellectual property, or classified information.
- The theft of research data from universities could impact future technological and scientific advancements.
Critical Infrastructure Risks:
- Government systems often control critical infrastructure, making them prime targets for disruptive attacks.
- The potential for data breaches and system disruptions poses significant risks to national security and public services.
Mitigation and Recommendations:
Advanced Threat Detection:
- Organizations should implement advanced threat detection solutions capable of identifying sophisticated malware like “Auto-Color.”
Security Audits and Hardening:
- Regular security audits and system hardening are essential to identify and mitigate vulnerabilities.
Incident Response Planning:
- Develop and maintain robust incident response plans to address potential malware infections.
Network Monitoring:
- Closely monitor network traffic for unusual or suspicious activity.
Patching and Updating:
- Keep all Linux systems fully updated with the latest security patches.
The “Auto-Color” malware represents a significant threat, highlighting the ongoing evolution of cyberattacks targeting Linux systems. Organizations must remain vigilant and implement proactive security measures to protect against these sophisticated threats. As further information becomes available, bobsguide will continue to provide updates.














Leave a Reply