Bybit, the world’s second-largest cryptocurrency exchange, suffered a record-breaking $1.4 billion Ethereum heist, exposing vulnerabilities in even the most established platforms.
The cryptocurrency world is still reeling from the news of a massive security breach at Bybit, the world’s second-largest cryptocurrency exchange. In a shocking turn of events, hackers made off with a staggering $1.5 billion worth of Ethereum. Marking the largest cryptocurrency heist in history. This incident has sent shockwaves through the industry, raising serious questions about the security of digital assets and the vulnerability of even the most established platforms.
Anatomy of the attack
The attack transpired as Bybit was in the process of moving funds from a secure “cold” wallet (offline storage) to an online “warm” wallet. During this seemingly routine transfer, hackers exploited a vulnerability, manipulating the transaction process and diverting the funds to an address under their control. This manipulation involved a clever tactic: masking the signing interface. While the correct address was displayed, the hackers altered the underlying smart contract logic, essentially tricking Bybit’s operators into signing off on a malicious transaction.
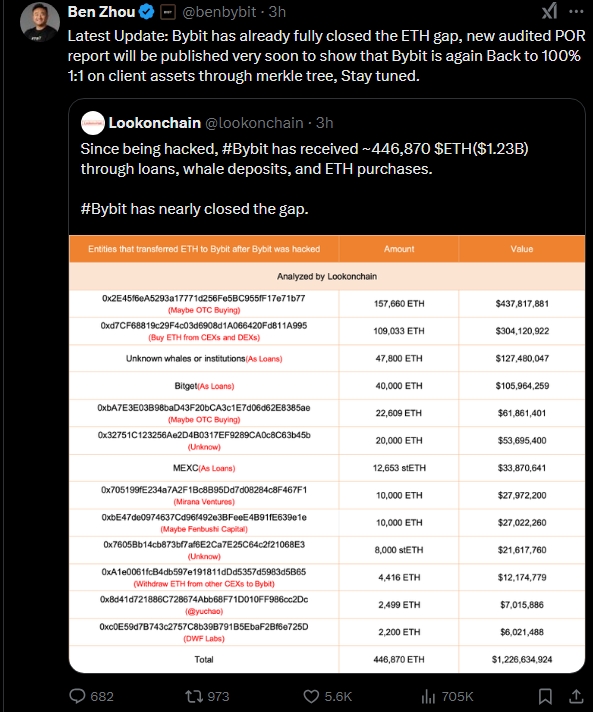
Bybit CEO Ben Zhou confirmed the loss of 401,000 ETH coins, valued at approximately $1.4 billion at the time. The stolen assets included various Ethereum-based tokens, such as staked ETH (stETH) and Mantle Staked ETH (mETH). Adding to the intrigue, blockchain analysis firms have linked the attack to North Korea’s Lazarus Group. A state-sponsored hacking organization with a history of targeting cryptocurrency exchanges. If their involvement is confirmed, this attack would significantly bolster North Korea’s crypto holdings. Raising concerns about the potential use of these stolen digital assets to fund illicit activities.
Damage control and reassurance
Bybit’s response to the crisis was swift, transparent, and multifaceted. Within 30 minutes of the attack, CEO Ben Zhou took to social media to address the community, assuring users that Bybit remained solvent and that all customer assets were fully backed. He emphasized that the exchange had sufficient liquidity to honor withdrawals and weather the storm, despite a surge in withdrawal requests following the hack. To further reassure users, Zhou conducted a live stream an hour after the incident, providing real-time updates and detailed explanations.
Bybit also took several key actions to mitigate the damage and restore confidence:
- Maintaining operational continuity
- Efficient withdrawal processing.
- Securing bridge loans
- Collaboration with authorities
- Engaging blockchain forensic experts
- Launching a bounty program
- Collaboration for asset recovery
Industry support
In a show of solidarity, major cryptocurrency exchanges blocklisted the hacker’s wallets, preventing further movement of the stolen funds. Bybit also reassured users that their assets were safe with a 1:1 reserve guarantee, ensuring that client assets remained fully intact.
The path forward
Cybersecurity experts have been dissecting the Bybit breach, highlighting:
- The human element in security: Despite robust security measures like multi-signature wallets and cold storage, the Bybit hack demonstrated that human error and social engineering remain significant vulnerabilities. This highlights the importance of user awareness and training to prevent falling victim to phishing attacks and other social engineering tactics.
- Evolving attack methods: The attack showcased the increasing sophistication of cybercriminals, who are now employing advanced techniques like user interface manipulation to bypass traditional security controls. This underscores the need for continuous improvement in security protocols and the adoption of more advanced threat detection mechanisms.
- The need for comprehensive security: The incident underscores the importance of a comprehensive security strategy that encompasses not only technical safeguards but also operational security, employee training, and incident response planning. Including, implementing measures such as air-gapped signing systems, multiple layers of transaction verification, and endpoint detection and response (EDR) systems.
- Shift in attack focus: The Bybit hack exemplifies a shift in attacker focus from exploiting code vulnerabilities to targeting operational security and human factors. Requiring a more holistic approach to security, recognizing that even the most secure systems can be compromised through human error or manipulation.
- Blind signing vulnerability: The incident exposed the vulnerability of multi-signature wallets to “blind signing” attacks, where signers are deceived into approving malicious transactions without fully understanding the implications. Emphasizing the need for clear and unambiguous transaction information and the importance of careful verification before signing any transaction.
- Importance of user interface security: The Bybit hack drew attention to the role of user interface manipulation in facilitating the attack. This highlights the need for enhanced UI security measures to prevent attackers from manipulating what users see and deceiving them into taking actions that compromise their security.
- Real-yime prevention: Experts emphasize the need for a paradigm shift from incremental security improvements to real-time prevention. This involves implementing systems that can inspect every transaction in real-time, similar to how firewalls operate in traditional networks, to prevent malicious activities before they cause damage.
The Bybit cybersecurity breach serves as a stark wake-up call for the cryptocurrency industry. It highlights the need for continuous improvement in security practices, a proactive approach to mitigating evolving threats, and a deeper understanding of the human element in security. While Bybit’s response to the crisis has been lauded for its transparency and efficiency, the incident underscores the ongoing challenges in safeguarding digital assets and the need for constant vigilance.
The breach also had a noticeable impact on the cryptocurrency market, with Ethereum’s price dropping nearly 4% in the immediate aftermath. This reflects the interconnectedness of the crypto ecosystem and the potential for security breaches to affect market sentiment and asset values. As the cryptocurrency ecosystem continues to grow and mature, learning from such incidents and adapting security practices accordingly will be crucial to maintaining trust, stability, and user confidence in this rapidly evolving landscape.














Leave a Reply